Debugging Windows services
Prerequisites
- Windbg
- A burning wish to debug a service at startup-time instead of just attaching to the process after it has started.
This guide is mainly for Windows 10.
Same or very similar procedure works for pretty much all major versions (at least from XP and up) of Windows, but the gflags application might look a bit different for some versions of Windows.
Set global flags
Open gflags.exe at C:\Program Files (x86)\Windows Kits\10\Debuggers\x64\gflags.exe
Go to the tab Image file, type the process name of the service you’d like to debug.
Set “debugger” to whichever debugger you’d like, windbg in my case: C:\Program Files (x86)\Windows Kits\10\Debuggers\x64\windbg.exe -server tcp:port=5005 -c "g"
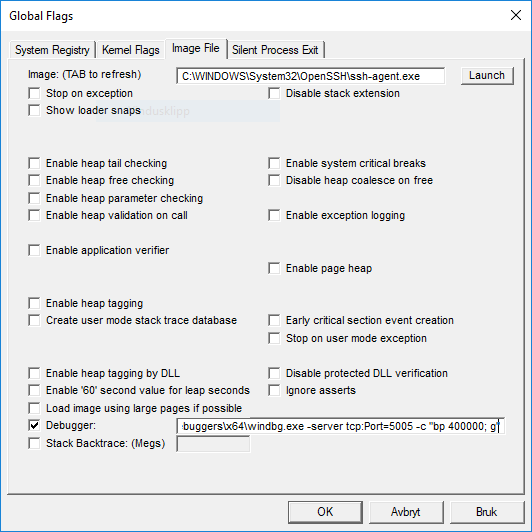
Which will make windbg the parent process of the image you specified when it launch. Windbg in this case spawns in the so-called “session 0” which is locked down and can’t be interacted with in the latest versions of Windows 10 (there is of course software that can still enable this). So instead of interacting with this particular UI instance of Windbg, we set it up as a remote session on port 5005. Specify some windbg commands in the -c argument like breakpoints and stuff that you’d like to debug.
Connecting to windbg
Right after (re)starting the server launch windbg from cmd: C:\Program Files (x86)\Windows Kits\10\Debuggers\x64\windbg.exe -remote tcp:Port=5005,Server=127.0.0.1
Do your thing, but remember, if you break in the OnStart function of the service, Windows will only give you 30 seconds to do your debugging before it kills your process.